Showing
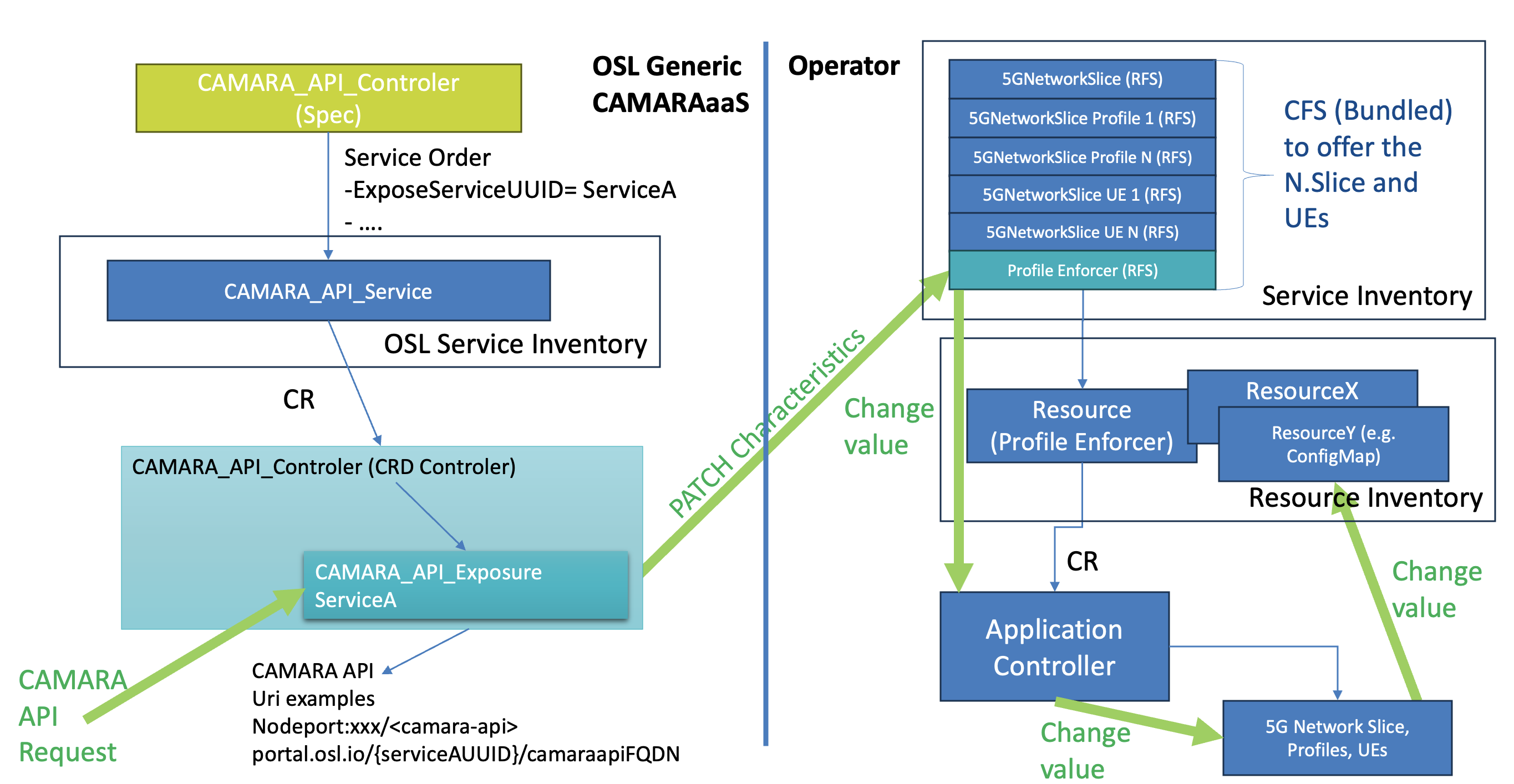
- Documentation/CAMARAaaS-Architecture.png 0 additions, 0 deletionsDocumentation/CAMARAaaS-Architecture.png
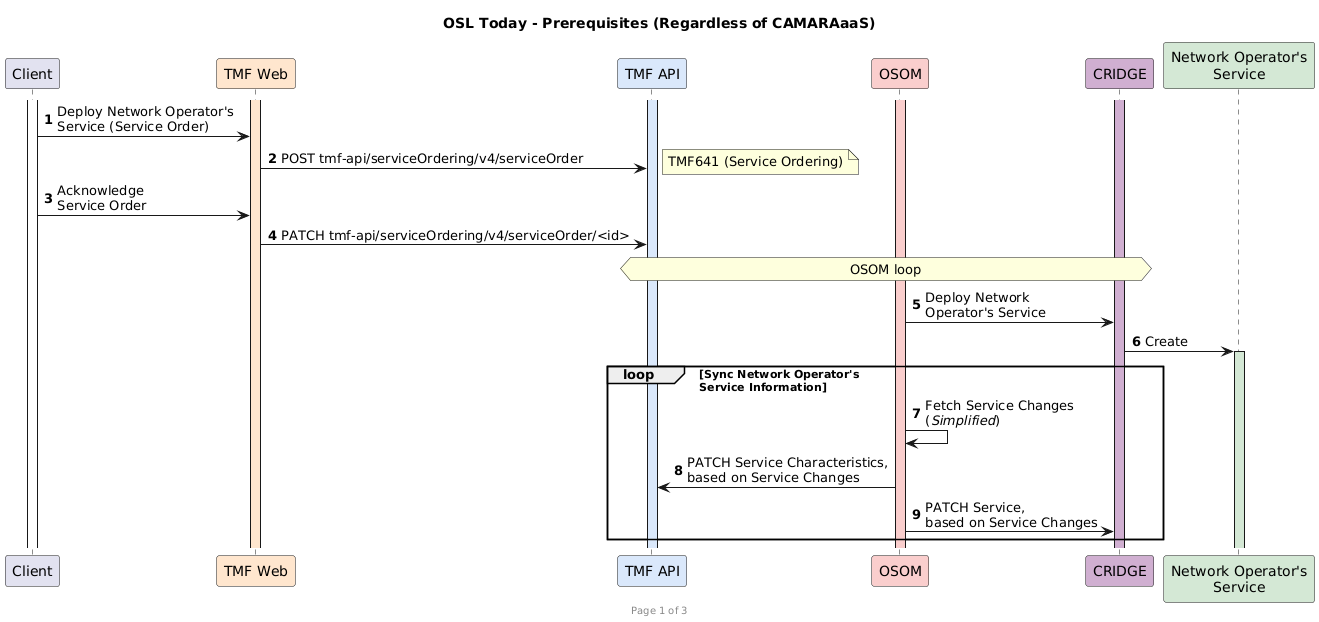
- Documentation/CAMARAaaS-Workflow-OSLToday.png 0 additions, 0 deletionsDocumentation/CAMARAaaS-Workflow-OSLToday.png
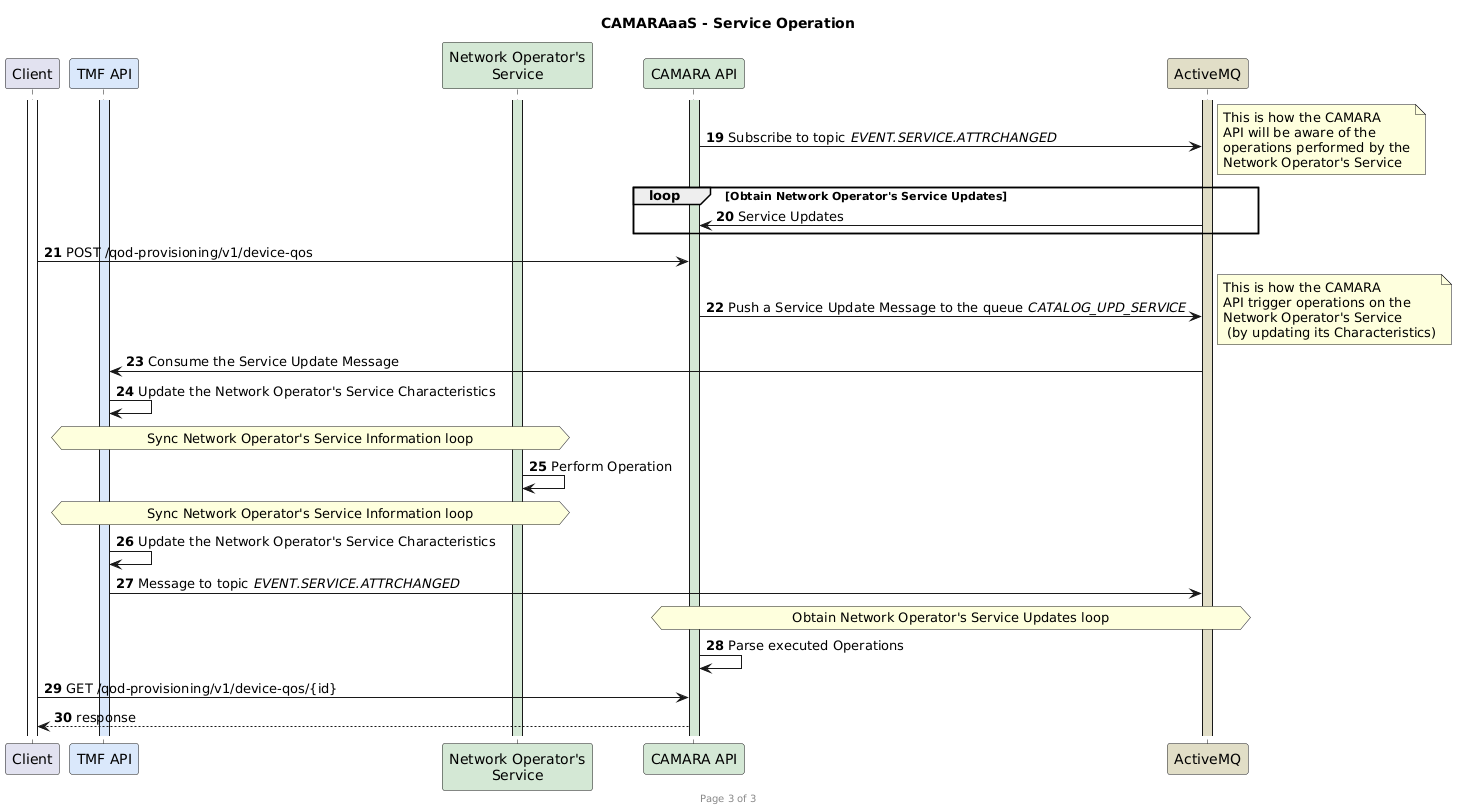
- Documentation/CAMARAaaS-Workflow-ServiceOperation.png 0 additions, 0 deletionsDocumentation/CAMARAaaS-Workflow-ServiceOperation.png
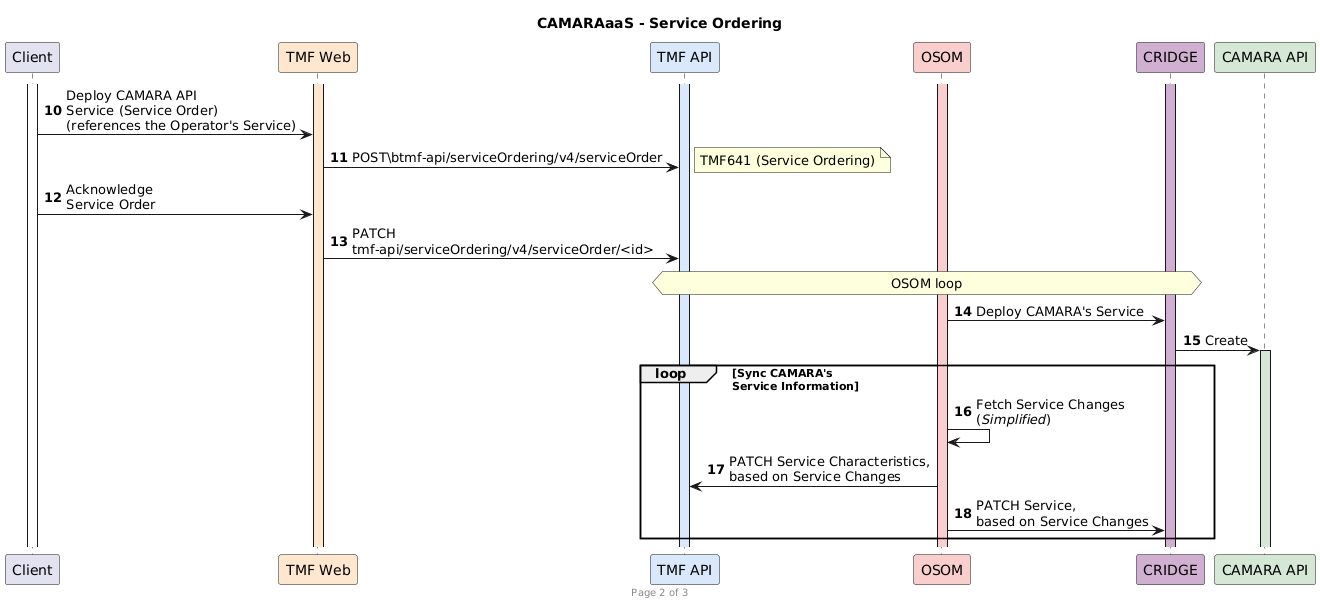
- Documentation/CAMARAaaS-Workflow-ServiceOrdering.png 0 additions, 0 deletionsDocumentation/CAMARAaaS-Workflow-ServiceOrdering.png
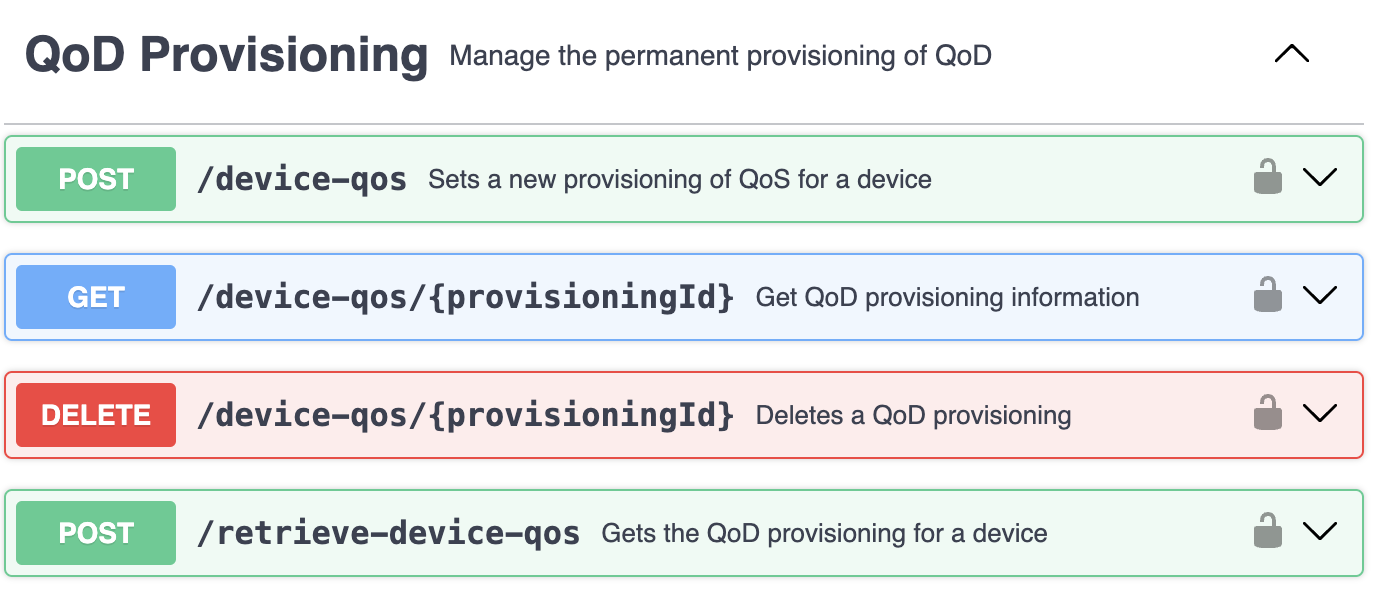
- QoDProvisioning/Documentation/Pictures/CAMARA-QoDProvisioning-API-Endpoints.png 0 additions, 0 deletions...ntation/Pictures/CAMARA-QoDProvisioning-API-Endpoints.png
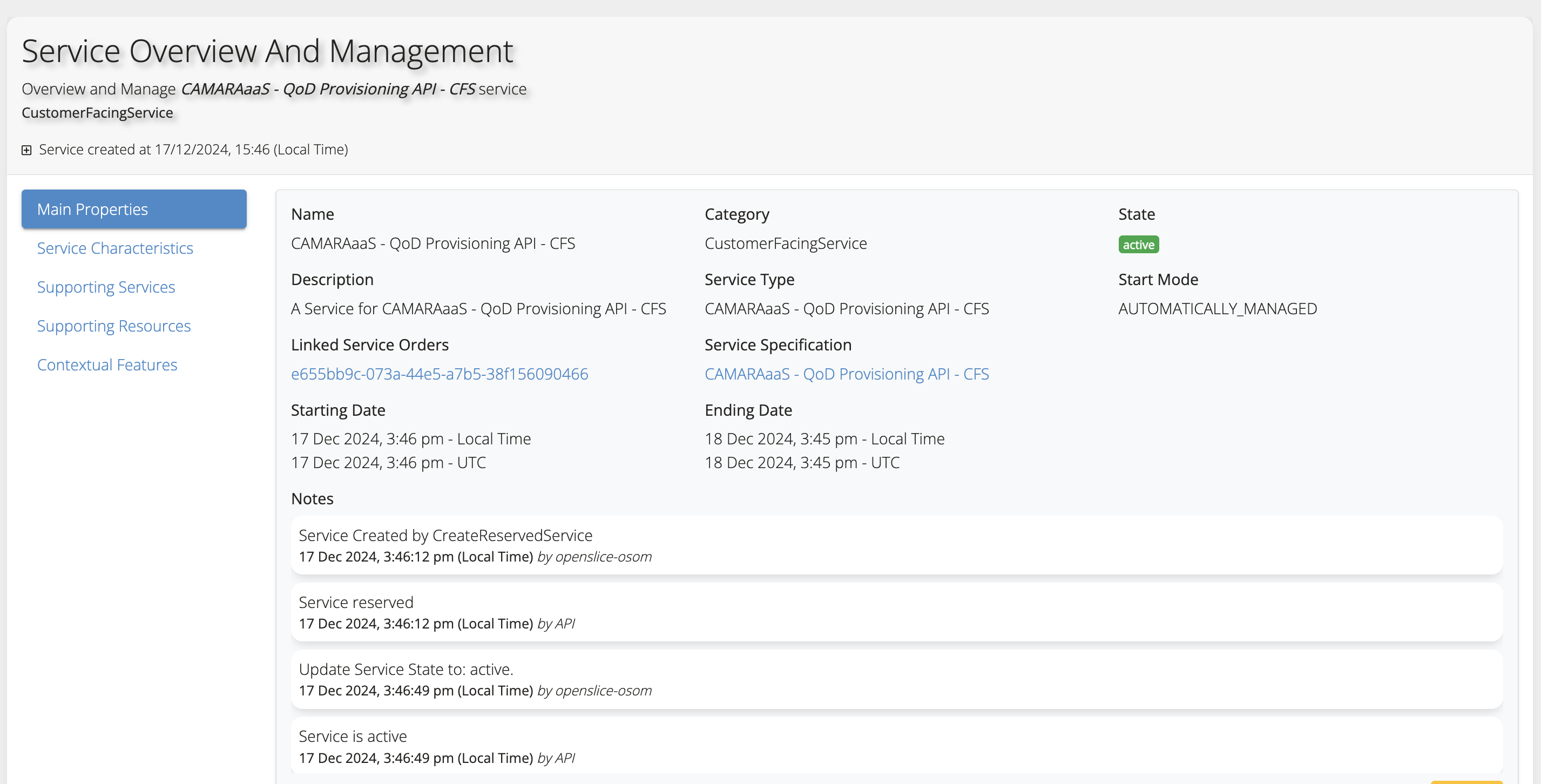
- QoDProvisioning/Documentation/Pictures/CAMARAaaS-QoD-Prov-API-Active-Services.png 0 additions, 0 deletions...ation/Pictures/CAMARAaaS-QoD-Prov-API-Active-Services.png
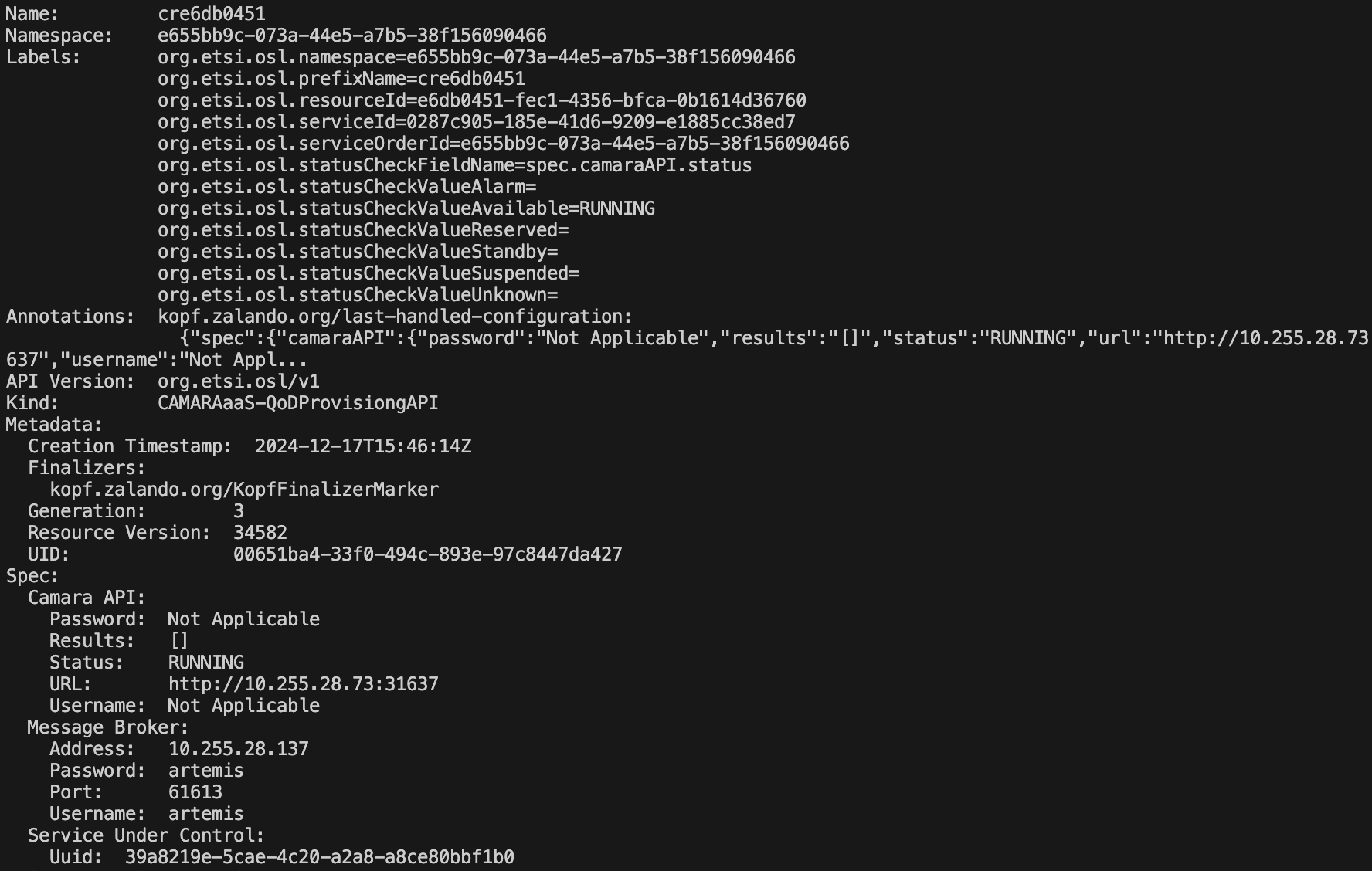
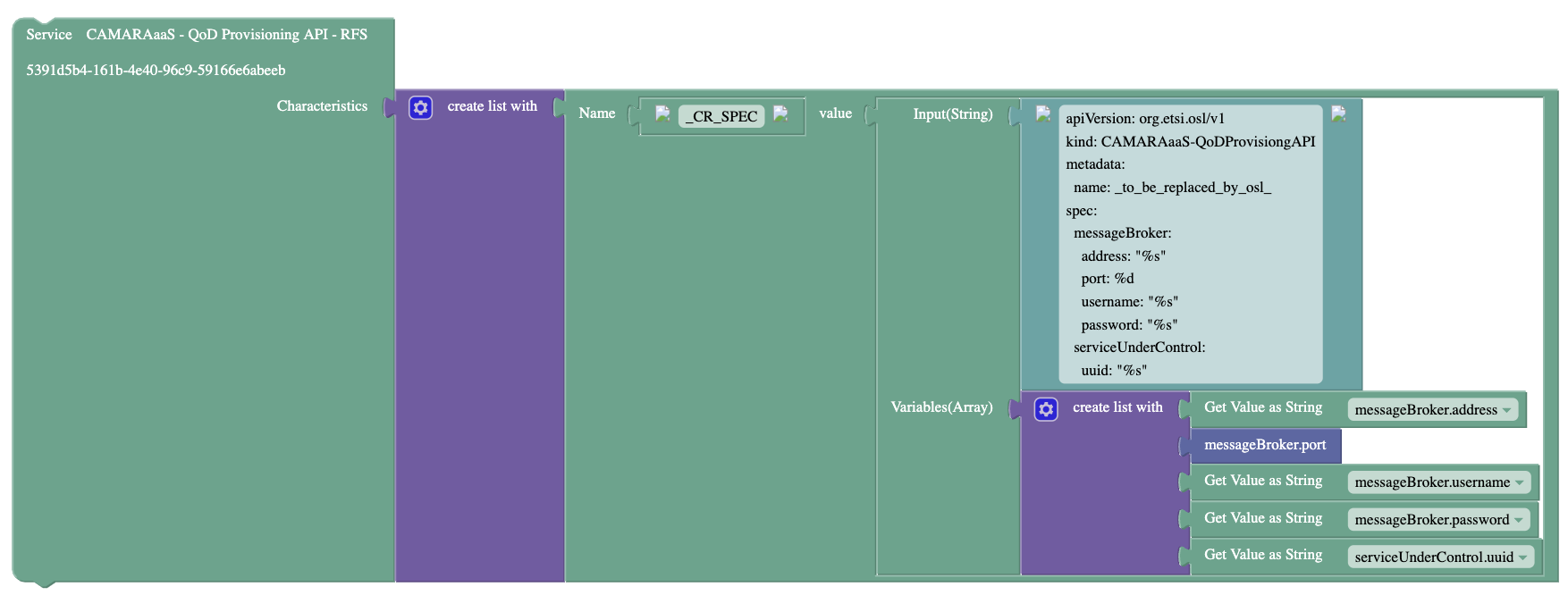
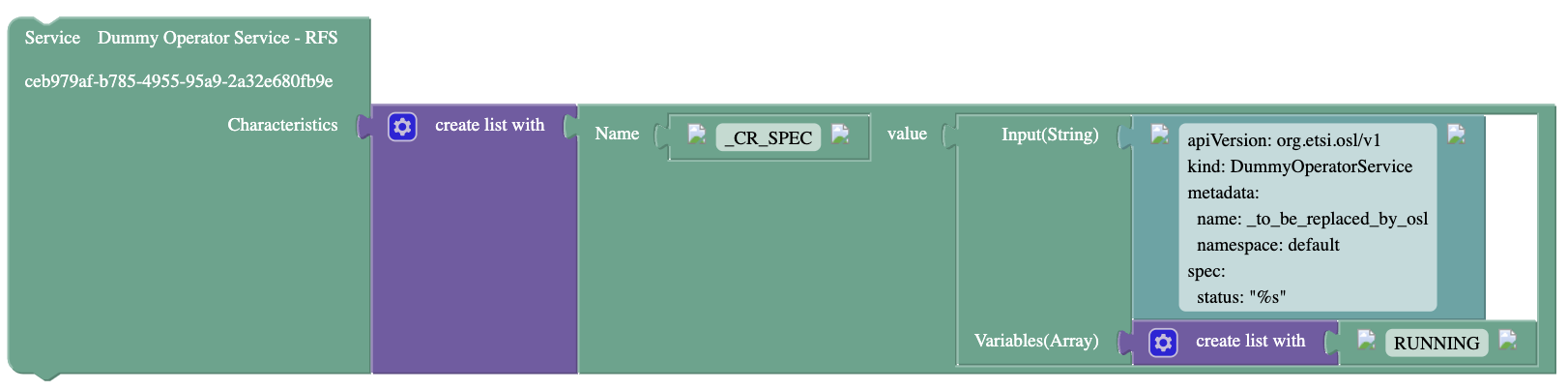
- QoDProvisioning/Documentation/Pictures/CAMARAaaS-QoD-Prov-API-CR.png 0 additions, 0 deletions...ning/Documentation/Pictures/CAMARAaaS-QoD-Prov-API-CR.png
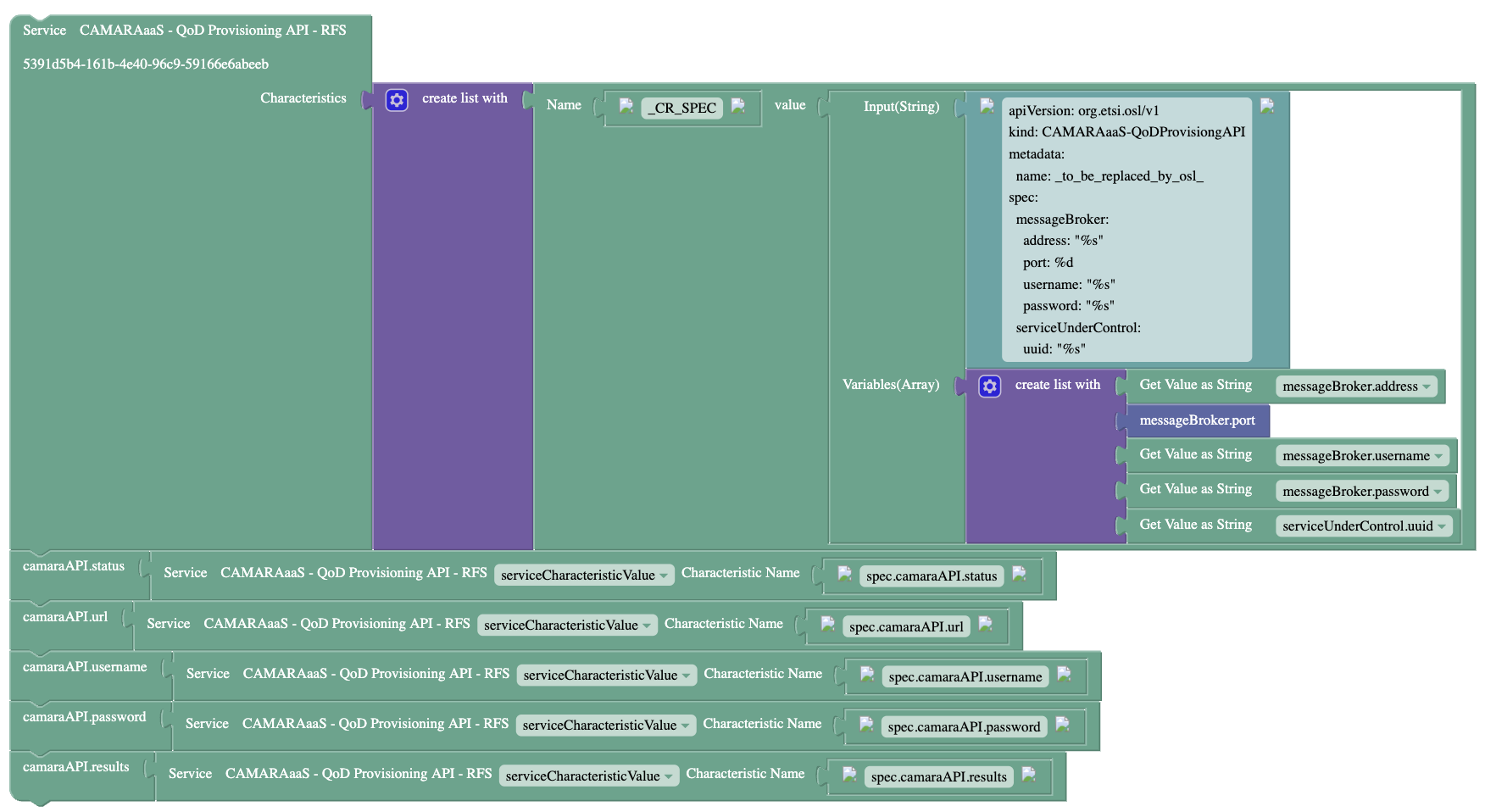
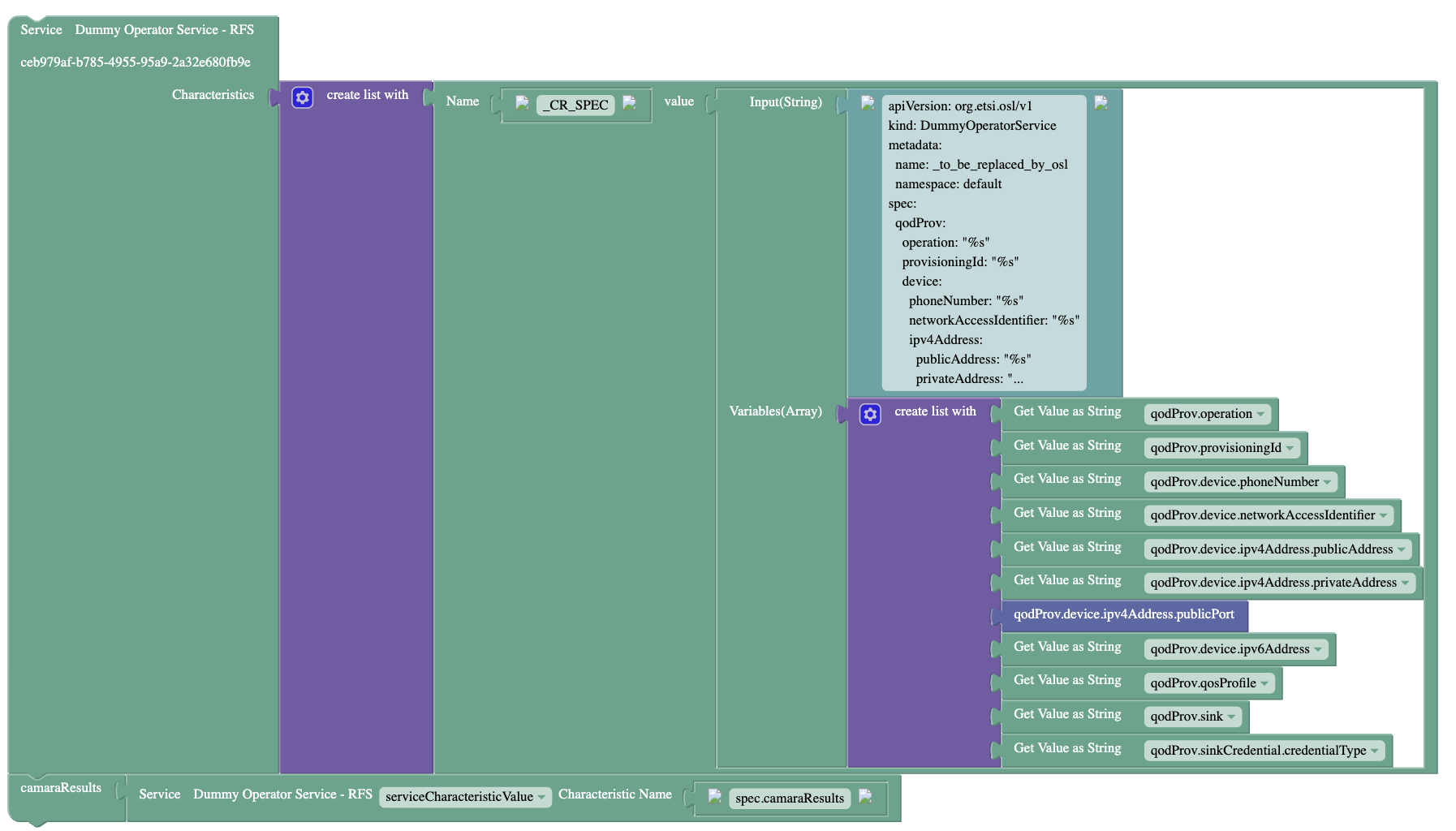
- QoDProvisioning/Documentation/Pictures/CAMARAaaS-QoD-Prov-API-Characteristics-After-CAMARA-Invoking.png 0 additions, 0 deletions...aS-QoD-Prov-API-Characteristics-After-CAMARA-Invoking.png
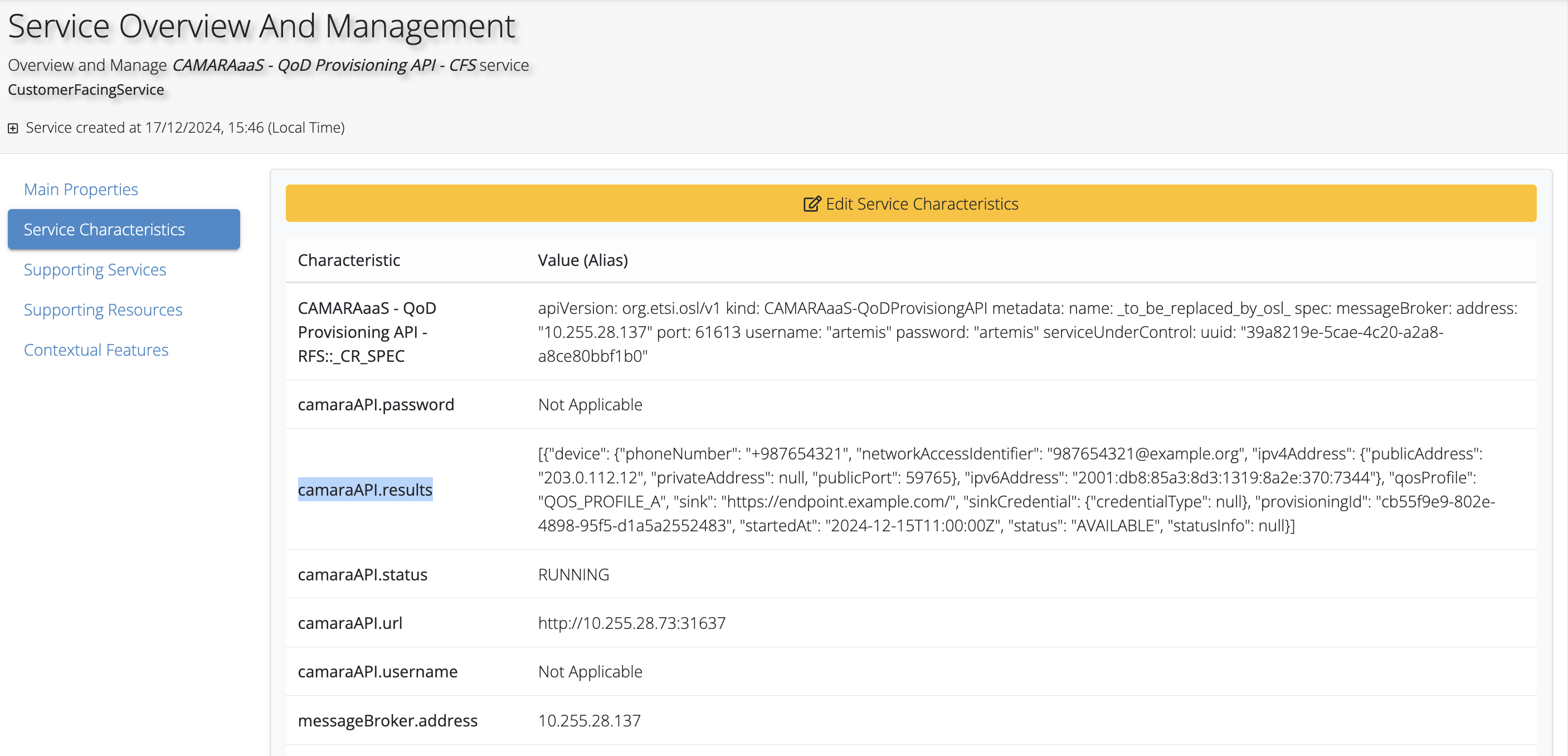
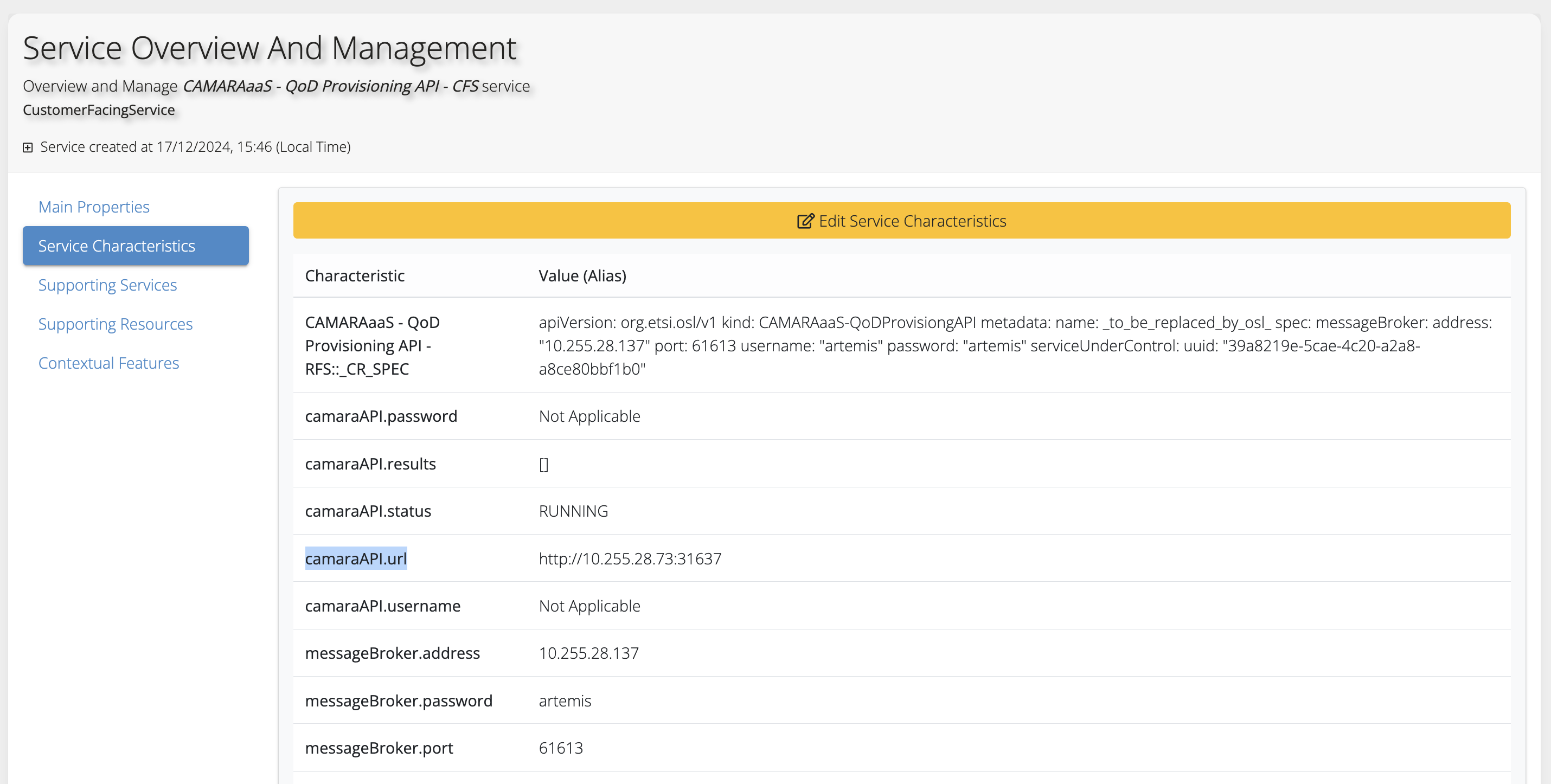
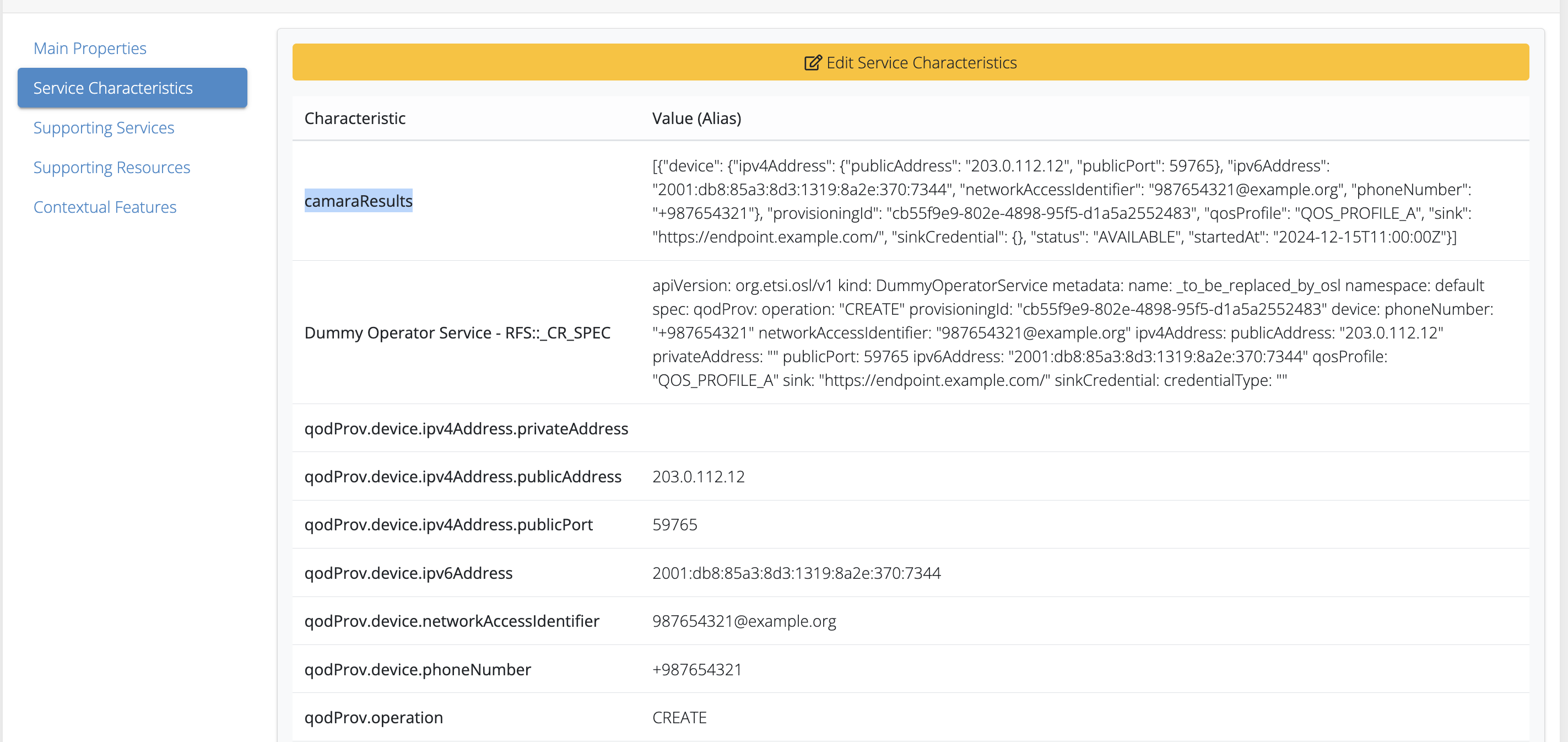
- QoDProvisioning/Documentation/Pictures/CAMARAaaS-QoD-Prov-API-Characteristics.png 0 additions, 0 deletions...ation/Pictures/CAMARAaaS-QoD-Prov-API-Characteristics.png
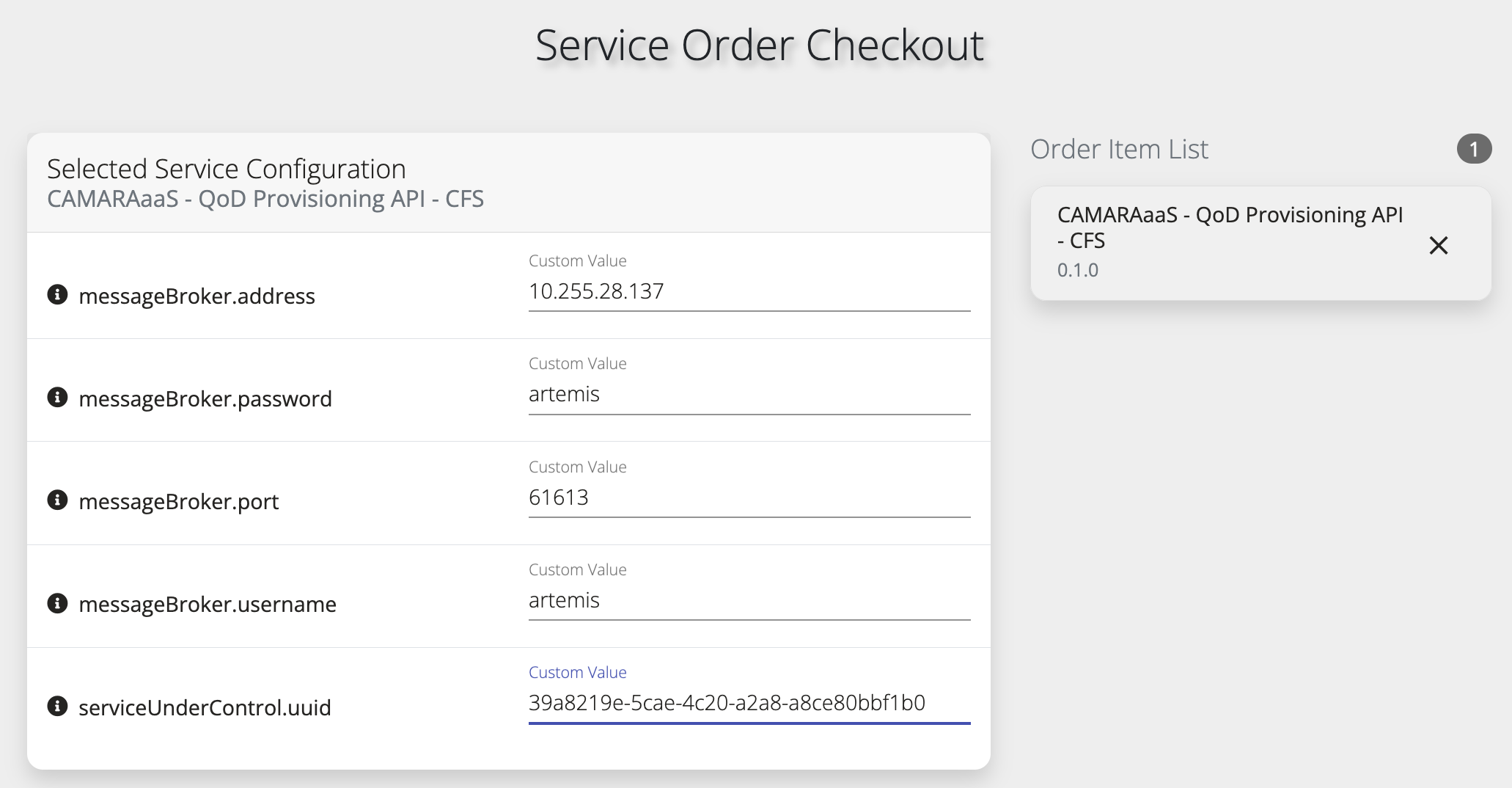
- QoDProvisioning/Documentation/Pictures/CAMARAaaS-QoD-Prov-API-Ordering.png 0 additions, 0 deletions...ocumentation/Pictures/CAMARAaaS-QoD-Prov-API-Ordering.png
- QoDProvisioning/Documentation/Pictures/CAMARAaaS-QoD-Prov-API-Pre-Provision-Rule.png 0 additions, 0 deletions...on/Pictures/CAMARAaaS-QoD-Prov-API-Pre-Provision-Rule.png
- QoDProvisioning/Documentation/Pictures/CAMARAaaS-QoD-Prov-API-Supervision-Rule.png 0 additions, 0 deletions...tion/Pictures/CAMARAaaS-QoD-Prov-API-Supervision-Rule.png
- QoDProvisioning/Documentation/Pictures/DummyOperatorService-Characteristics-After-CAMARA-Invoking.png 0 additions, 0 deletions...OperatorService-Characteristics-After-CAMARA-Invoking.png
- QoDProvisioning/Documentation/Pictures/DummyOperatorService-Pre-Provision-Rule.png 0 additions, 0 deletions...tion/Pictures/DummyOperatorService-Pre-Provision-Rule.png
- QoDProvisioning/Documentation/Pictures/DummyOperatorService-Supervision-Rule.png 0 additions, 0 deletions...tation/Pictures/DummyOperatorService-Supervision-Rule.png
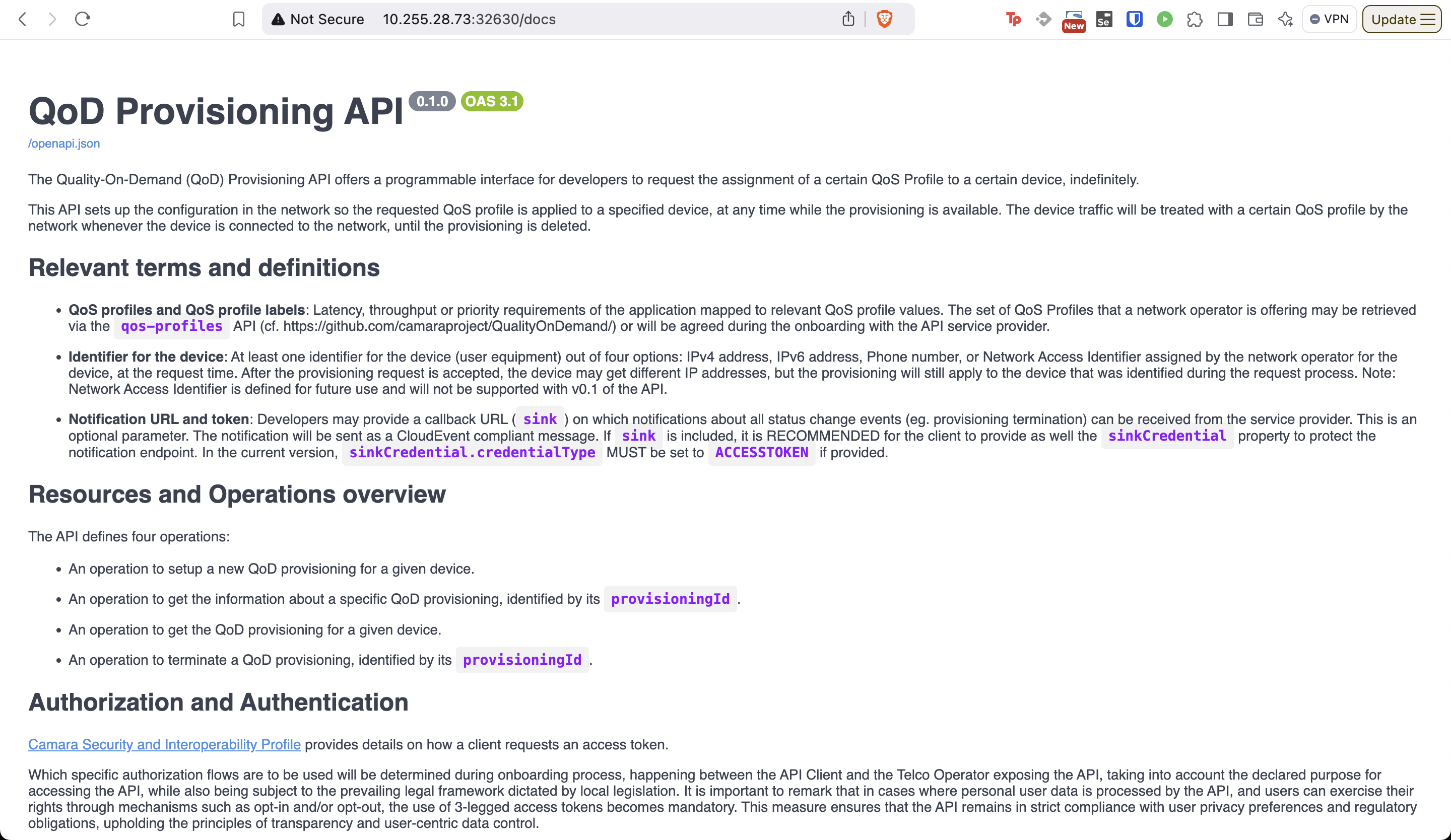
- QoDProvisioning/Documentation/Pictures/QoDProvisioningAPI-Docs.png 0 additions, 0 deletions...ioning/Documentation/Pictures/QoDProvisioningAPI-Docs.png
- QoDProvisioning/README.md 400 additions, 0 deletionsQoDProvisioning/README.md
- README.md 25 additions, 76 deletionsREADME.md
Documentation/CAMARAaaS-Architecture.png
0 → 100644
479 KiB
70 KiB
99.4 KiB
65.4 KiB
463 KiB
262 KiB
475 KiB
412 KiB
222 KiB
153 KiB
277 KiB
457 KiB
98.3 KiB
745 KiB
QoDProvisioning/README.md
0 → 100644