Showing
- doc/images/flows_invoker_check_authentication.jpg 0 additions, 0 deletionsdoc/images/flows_invoker_check_authentication.jpg
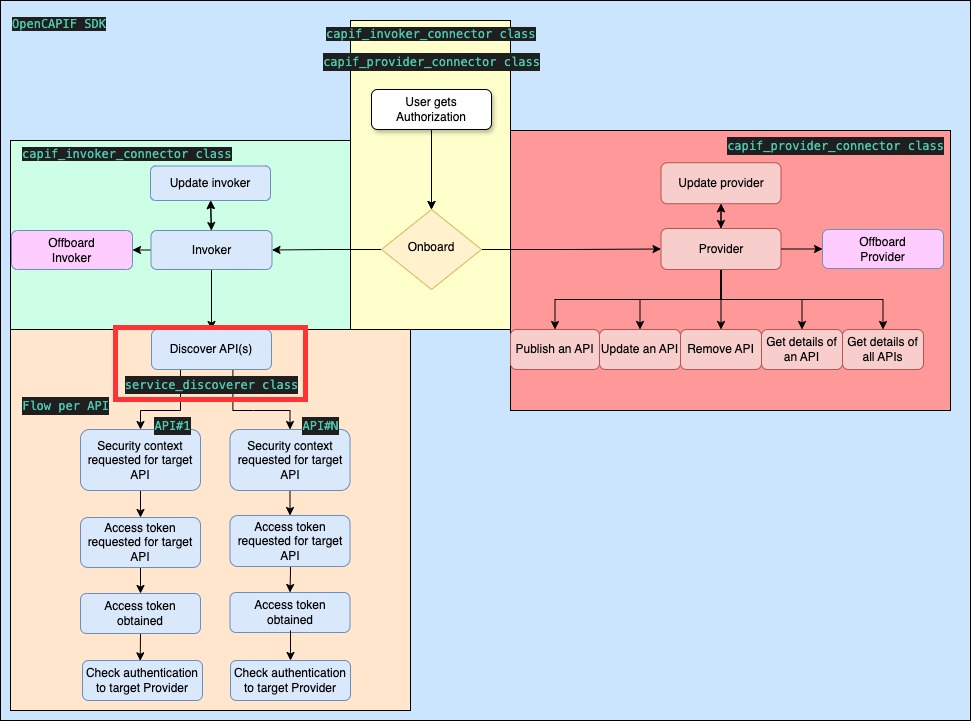
- doc/images/flows_invoker_discover.jpg 0 additions, 0 deletionsdoc/images/flows_invoker_discover.jpg
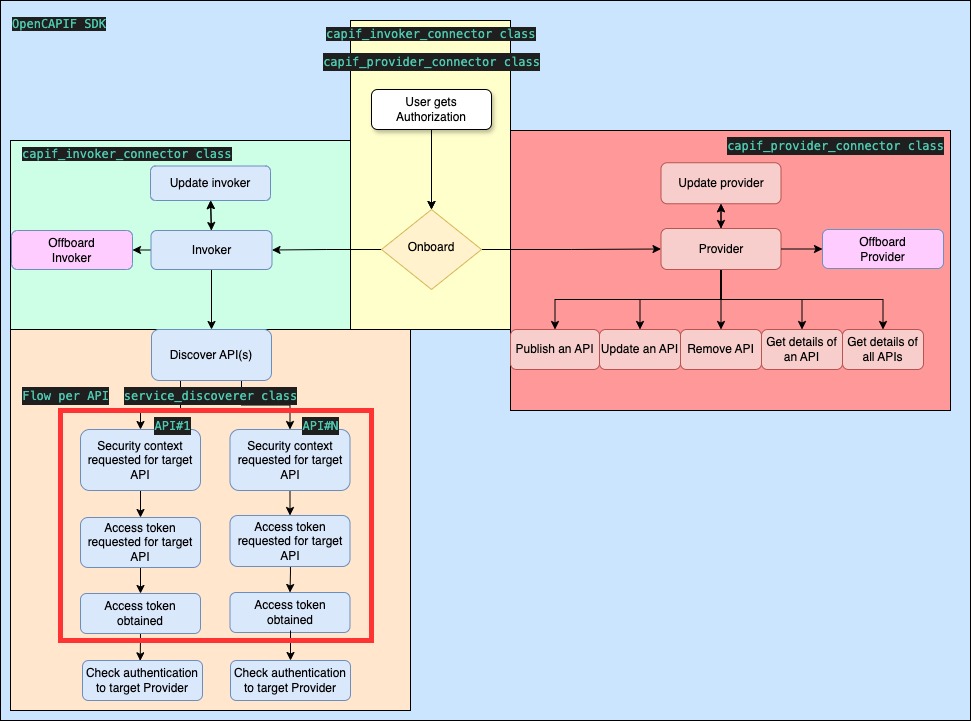
- doc/images/flows_invoker_get_tokens.jpg 0 additions, 0 deletionsdoc/images/flows_invoker_get_tokens.jpg
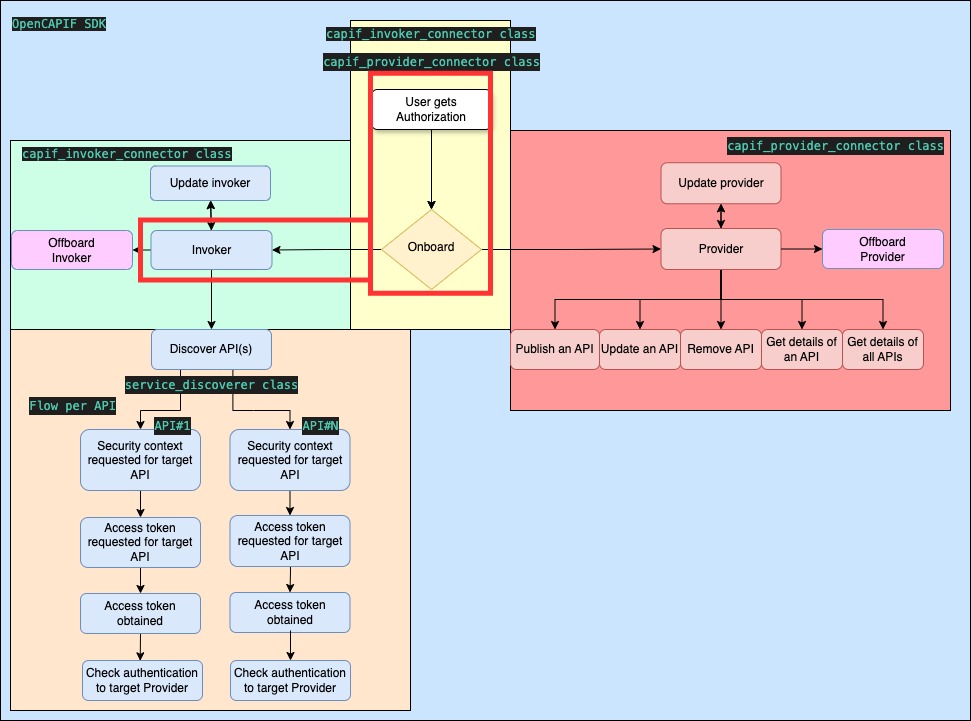
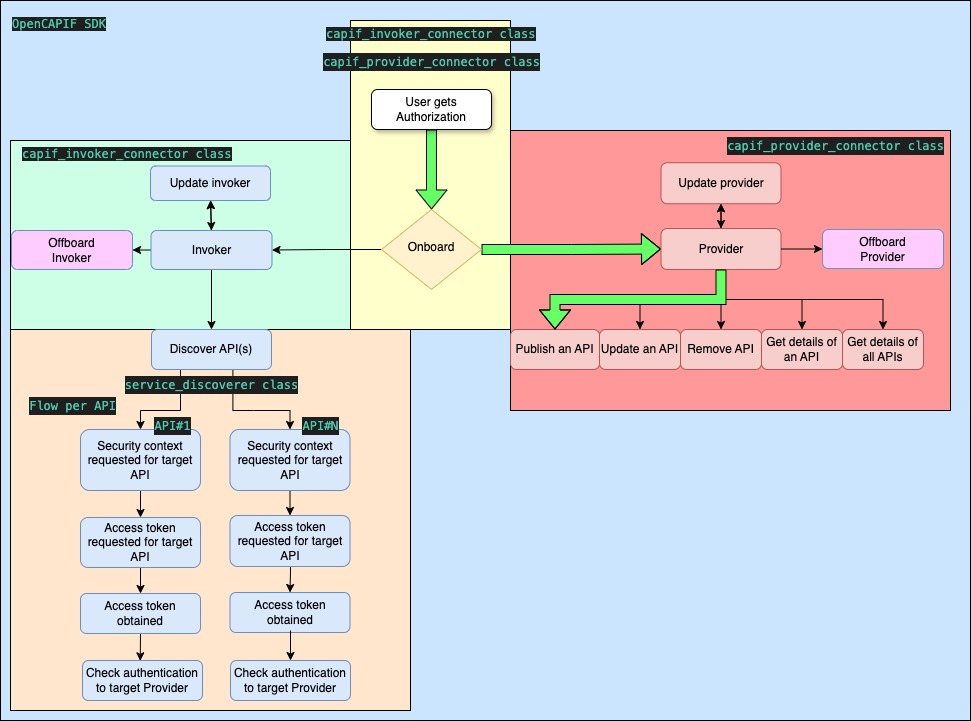
- doc/images/flows_invoker_onboard.jpg 0 additions, 0 deletionsdoc/images/flows_invoker_onboard.jpg
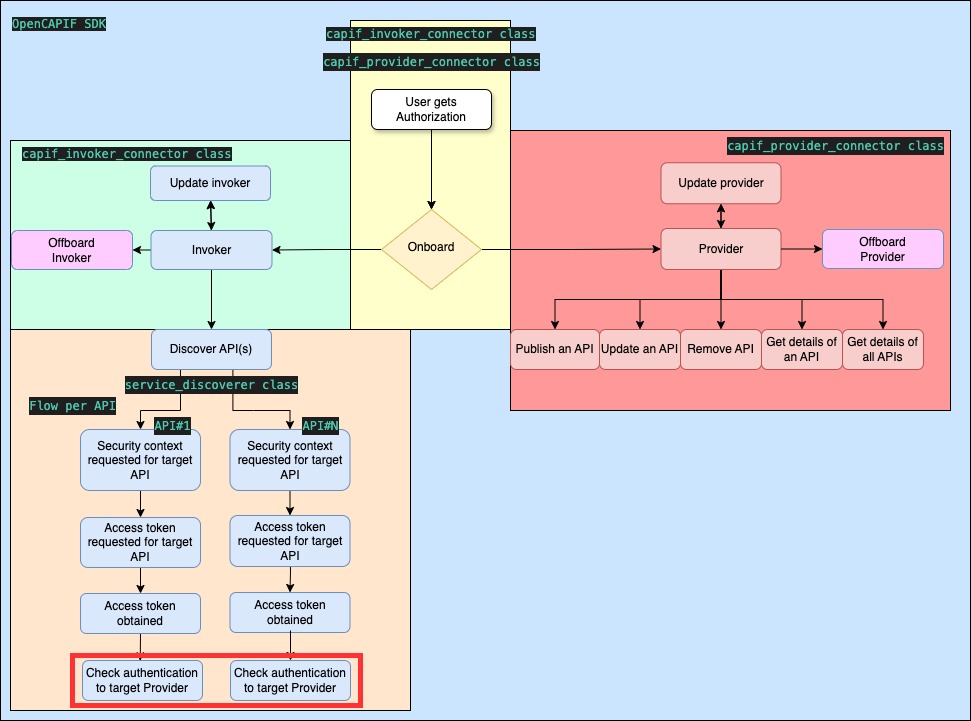
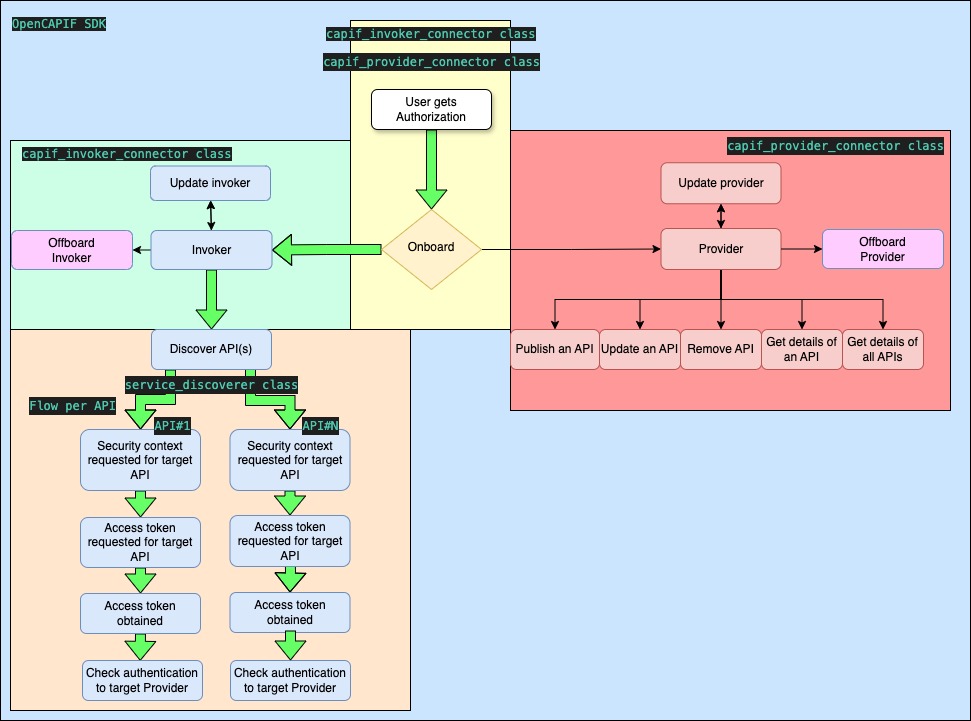
- doc/images/flows_invoker_path.jpg 0 additions, 0 deletionsdoc/images/flows_invoker_path.jpg
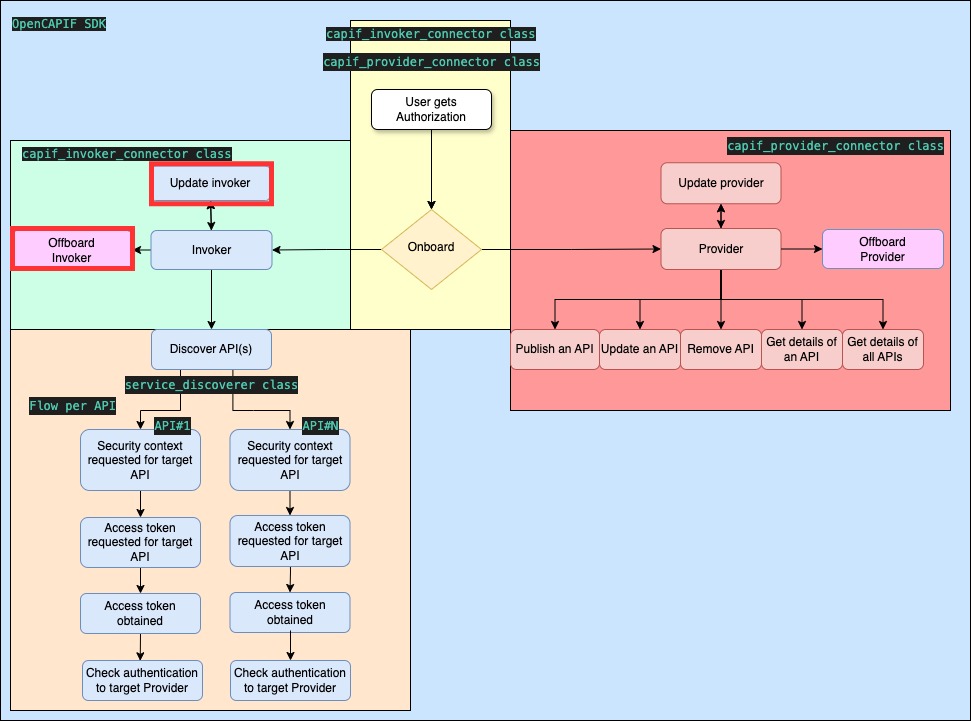
- doc/images/flows_invoker_update_offboard.jpg 0 additions, 0 deletionsdoc/images/flows_invoker_update_offboard.jpg
- doc/images/flows_provider_onboard.jpg 0 additions, 0 deletionsdoc/images/flows_provider_onboard.jpg
- doc/images/flows_provider_path.jpg 0 additions, 0 deletionsdoc/images/flows_provider_path.jpg
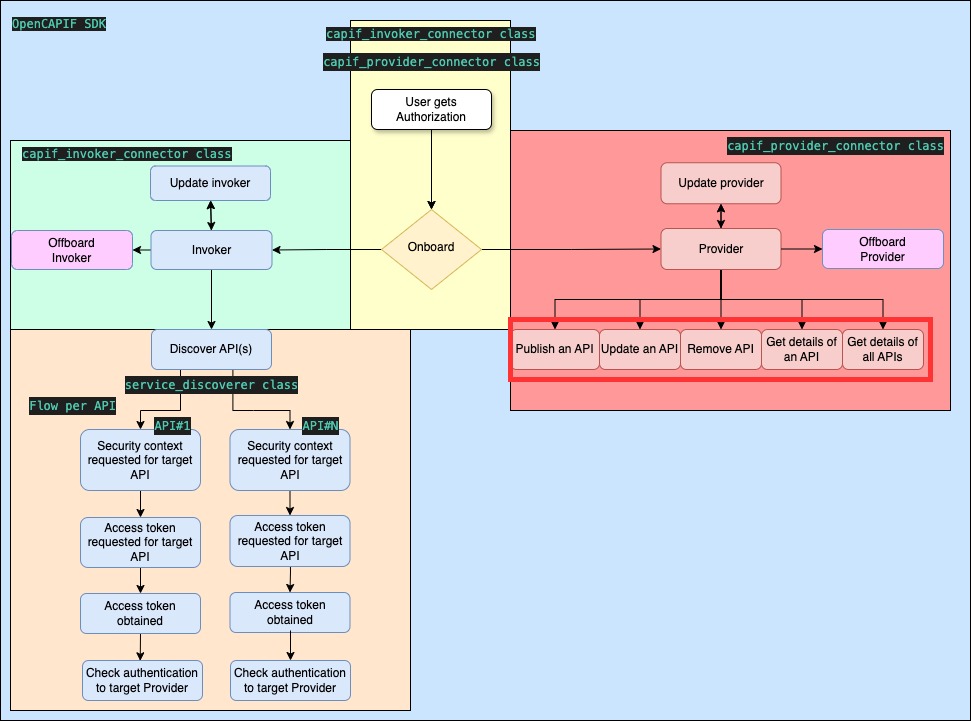
- doc/images/flows_provider_publish_functions.jpg 0 additions, 0 deletionsdoc/images/flows_provider_publish_functions.jpg
- doc/images/flows_provider_update_offboard.jpg 0 additions, 0 deletionsdoc/images/flows_provider_update_offboard.jpg
- doc/images/flows_updated_opencapif.jpg 0 additions, 0 deletionsdoc/images/flows_updated_opencapif.jpg
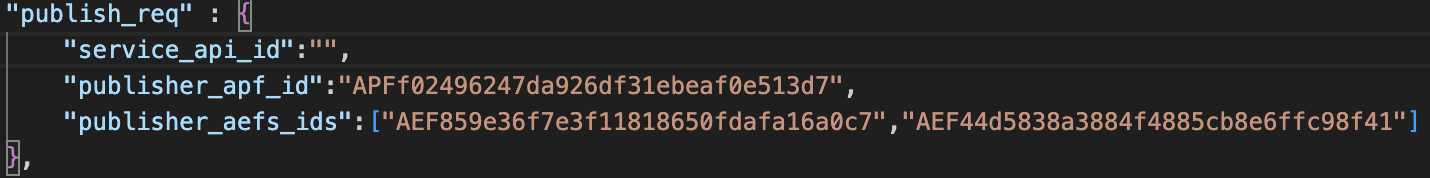
- doc/images/publish_req_example.png 0 additions, 0 deletionsdoc/images/publish_req_example.png
- doc/sdk_configuration.md 2 additions, 1 deletiondoc/sdk_configuration.md
- doc/sdk_full_documentation.md 99 additions, 10 deletionsdoc/sdk_full_documentation.md
- network_app_samples/network_app_invoker_sample/capif_sdk_config_sample.json 10 additions, 1 deletion...s/network_app_invoker_sample/capif_sdk_config_sample.json
- network_app_samples/network_app_provider_sample/capif_sdk_config_sample.json 10 additions, 1 deletion.../network_app_provider_sample/capif_sdk_config_sample.json
- opencapif_sdk/__init__.py 3 additions, 1 deletionopencapif_sdk/__init__.py
- opencapif_sdk/capif_event_feature.py 435 additions, 0 deletionsopencapif_sdk/capif_event_feature.py
- opencapif_sdk/capif_invoker_connector.py 70 additions, 34 deletionsopencapif_sdk/capif_invoker_connector.py
- opencapif_sdk/capif_logging_feature.py 287 additions, 0 deletionsopencapif_sdk/capif_logging_feature.py
99.9 KiB
99.8 KiB
101 KiB
doc/images/flows_invoker_onboard.jpg
deleted
100644 → 0
101 KiB
doc/images/flows_invoker_path.jpg
deleted
100644 → 0
104 KiB
99 KiB
102 KiB
doc/images/flows_provider_path.jpg
deleted
100644 → 0
101 KiB
101 KiB
98.9 KiB
98.4 KiB
doc/images/publish_req_example.png
deleted
100644 → 0
82.4 KiB
opencapif_sdk/capif_event_feature.py
0 → 100644
opencapif_sdk/capif_logging_feature.py
0 → 100644